Avoiding Email Hacks
Guest Columnist: Steve Feher, The Ridgefield Group
Every time we open email, we’re looking at communication that can drive business to our firm. Whether the email is from a vendor, customer, or colleague, we likely act quickly to respond and follow-through. Since we may often get emails from the same address or contact, we may sometimes act too quickly when we reply to an email. We may not notice that the email is, in fact, not from whom we think. Such a message may ask us for payment details, password credentials, or other seemingly innocent and important details what we’d typically jump right on. The desire to reply quickly can open the opportunity for headaches.
What can a small business do to combat emails that are so good at faking us out? How can we separate the right emails from the wrong emails? How can we avoid being tricked into divulging critical data to false contacts?
In short, it’s important to remember that no one is perfectly secure. Our banks, our investments, our medical data and other data might be well secured, but we’re all subject to the greatest and most likely risky behavior; that of human beings. This is what makes email phishing schemes and hack attempts so attractive to perpetrators. They simply ask us for the information they want and we (unintentionally) deliver it to them. It’s charming, elegant, clean, and simple.
All businesses, including the Chamber of Commerce, are susceptible to this. In fact, it’s happened over the last few weeks to unsuspecting chamber members and thus, this article was authored to help create an educational opportunity for us all.
Below is a screen capture of an email that was received by one of our fellow members of the Chamber (their name is redacted for privacy). This email “came from” the Chamber Of Commerce and so the member of course wanted to act on this. How many things can you see wrong with this email? Take a minute and try to count.
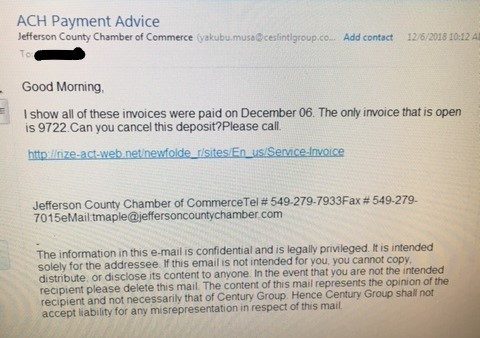
If you found more than four big errors, you’re pretty sharp! Let’s dissect this a bit and see what you found.
ITEM 1 – Subject Line
While we can’t always doubt a subject line, it’s interesting to note that this subject is a little uncommon for the Chamber of Commerce. “ACH Payment Advice” sounds like it might come from your bank, but that would be unexpected for the Chamber. Maybe this alone isn’t enough to make us suspicious, but it’s certainly odd.
ITEM 2 – Sending Email account
Note that the email address that’s apparently used to send this email from the Chamber is yakubu.musa@ceslintlgroup.com. Last we knew, no one with that name worked at the Chamber. Are they a new employee? Perhaps… but the domain name ceslintlgroup.com is surely NOT the Chamber’s address. If you look up this domain, you’ll find it resolves to a website promoting a Nigerian energy conglomerate. The oddity is increasing.
ITEM 3 – Content of the email
Did we recently pay the Chamber of Commerce on December 6? Does this even make sense? And, if there’s an open invoice, why would we be asked to “cancel the deposit”?
ITEM 4 – Link
The link that is presented has a ‘top domain’ that’s new; http://rize-act-web.net is surely NOT the Chamber of Commerce – our suspicions ought to be on hyper alert now, especially since the link is not secure (note the absence of the httpS:// in the URL; the ‘s’ should be where the green arrow points). This URL is not encrypted, yet it is supposedly referring us to an invoice.
ITEM 5 – Phone Number
Have we ever dialed a Jefferson County Ohio business with a 549 area code? A quick Google search shows us that the 549 Area Code is Des Moines, Iowa. Surely the Chamber doesn’t use those numbers.
ITEM 6 – Disclaimer
The email footer has a disclaimer from a company called the “Century Group” which is unlikely for an email that originates from the Chamber.

Individual Vigilance is Important
Once we begin to investigate this email, it seems fairly clear that it is not legitimate. No specialized training is needed here; all the items above were simply discovered by observation and some healthy skepticism. If we remember that not every email we receive is a genuine message and not every request merits our response, we become less likely to be a victim of phishing attacks.
While spam filters, malware scans, and antivirus tools are important (and you should certainly use them), the best defense against attacks may very well be our own vigilance. By training ourselves to question our own inbox, we can help prevent problems and their painful consequences.
